
SECURE IDENTITY, ACCESS & DATA EVERYWHERE
PRIVILEGED ACCESS MANAGEMENT
Controlling privileged accounts
WALLIX PAM
WALLIX PAM is designed to manage and secure privileged accounts within an organization’s IT and OT environments. Privileged accounts are those with elevated permissions used by people often held by administrators, IT personnel, or third-party vendors, but also software and machines, that provide access to critical systems and sensitive data. WALLIX PAM focuses on controlling, monitoring, and securing access to these privileged accounts to mitigate the risk of unauthorized access, data breaches, or misuse of sensitive information.
WALLIX Remote Access
Most businesses rely on external service providers to perform remote tasks that require privileged access to their IT or OT network. Half of them do not have an inventory of third-party access to their network, have little or no visibility and control over their remote digital access. WALLIX One Remote Access helps meet the new access requirements for provisioning and enabling secure access to external service providers who need to access critical infrastructure managed by WALLIX One.
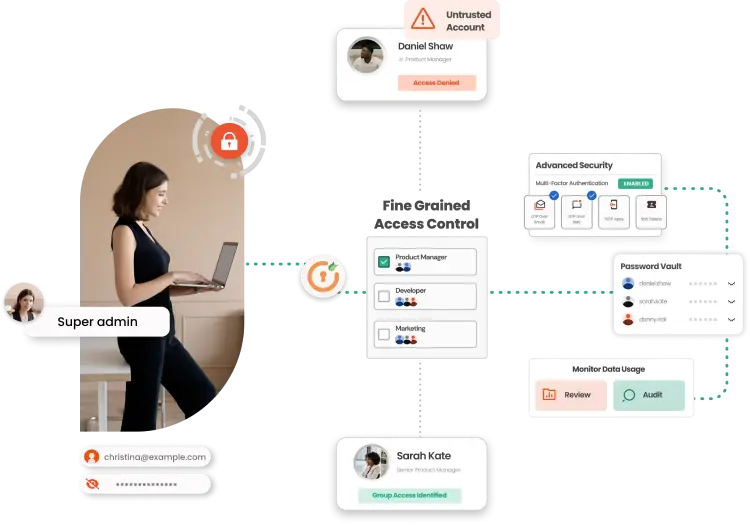

IDENTITY AND ACCESS MANAGEMENT
Seamlessly securing all access
WALLIX IDaaS
Digital transformation has significantly altered our perception of identity. Balancing competing priorities such as eciency, productivity, and security across a diverse range of in-house and cloud-based applications has intensified the responsibilities of IT teams. They now face a more significant challenge in accurately identifying individuals accessing corporate systems and ensuring secure and ecient access to maintain seamless business operations. WALLIX One IDaaS addresses the challenges and risks associated with authenticating employees and contractors to corporate resources remotely
WALLIX MFA
Your users’ names and passwords can be hacked or cracked: using a multi-factor authentication solution increases authentication security. Eliminate password risks and have your privileged users use multiple credentials. multi-factor proof-based verification of a user’s identity provides the control needed to access corporate systems.
IDENTITY AND ACCESS GOVERNANCE
Access reviews and entitlement control
WALLIX IAG
With WALLIX IAG, regaini Identity and Access Governance (IAG) enables the implementation of security policies for managing the rights assigned to employees and contractors, ensuring their legitimacy. Users should only access IT system resources essential for their business requirements and in accordance with their role-based rights. WALLIX IAG enables you to map and control access rights daily, aligning closely to your employees’ movements. It helps you save time through high-performance management of your business teams’ rights, with a collaborative vision and “automated” execution of review campaigns






 Security Researcher – Chief Business Strategist
Security Researcher – Chief Business Strategist  Security Researcher – Chief Business Strategist
Security Researcher – Chief Business Strategist  Security Researcher – ICS / SCADA System Security
Security Researcher – ICS / SCADA System Security Security Researcher – Web / Mobile / Windows
Security Researcher – Web / Mobile / Windows  Security Researcher – Web/ API / Mobile
Security Researcher – Web/ API / Mobile Security Researcher – Mobile & Web
Security Researcher – Mobile & Web Security Researcher – Mobile & Web
Security Researcher – Mobile & Web