
ZERO TRUST ACCESS SOLUTION PROTECTING YOUR USERS, DEVICES AND DATA, WHEREVER THE LOCATION
Identify. Control. Protect. Any user. Any device. Any data.
The SecurEnvoy Zero Trust Access Solution allows organisations to provide verifiable trust in every activity they perform. Our enterprise security solution delivers you a journey of identifying the user, device and location; discover exactly what data you have and where it is; classify that data effectively; control who has access to what data and what device; and then deliver your policy in control of data ensuring enhanced data protection. All with intelligent organisation control and monitoring with SecurEnvoy to support you on your journey.
Access Management Solution
SecurEnvoy’s Access Management Solution meets the challenge of managing user access across a wide range of systems and applications. The first step in your zero-trust approach to security. SecurEnvoy’s Access Management Solution ensures that only authorised users have access to the information they need, when they need it.
SecurEnvoy’s Access Management Solution will:
- Streamline access to applications by users regardless of device or location
- Secure employee, partner and customer data easily through a single platform
- Enable you to grant and revoke access when needed ensuring data compliance
- Reduce administration overheads from helpdesk calls and password reset requests
- Improve productivity for users and IT staff and reduce resource time and costs
- Mitigate risk of unauthorised access and aid regulatory compliance
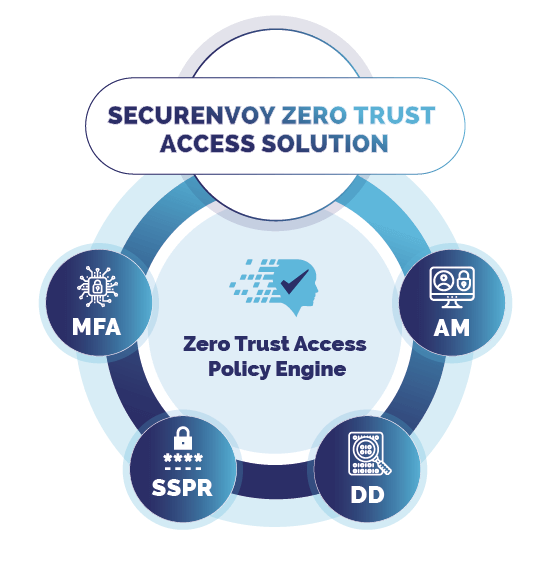
Multi-Factor Authentication Solutions (MFA)
Passwords alone are not strong enough to protect your business-critical data and assets. The rudimentary “username and password” approach to security is easy prey for cybercriminals. SecurEnvoy MFA provides an additional layer of security via two-factor or multi-factor authentication.
Our multi-factor authentication solution is easy to adopt and simple to use for you and your users. SecurEnvoy MFA lets you choose and set up any personal device or hardware token for authentication, making it simple for users to accept authentication requests with the device and method that suits them and your business best.
Data Discovery Platform
With SecurEnvoy Data Discovery you can simply track sensitive data from the time it is created, through to modification and deletion.
Data users are automatically alerted to the discovery of sensitive data by email, in real time.
Users who understand the data and its context can check and remediate sensitive data themselves, becoming active members of the data security team.
Your staff are actively involved and constantly reminded of the importance of data protection.





 Security Researcher – Chief Business Strategist
Security Researcher – Chief Business Strategist  Security Researcher – Chief Business Strategist
Security Researcher – Chief Business Strategist  Security Researcher – ICS / SCADA System Security
Security Researcher – ICS / SCADA System Security Security Researcher – Web / Mobile / Windows
Security Researcher – Web / Mobile / Windows  Security Researcher – Web/ API / Mobile
Security Researcher – Web/ API / Mobile Security Researcher – Mobile & Web
Security Researcher – Mobile & Web Security Researcher – Mobile & Web
Security Researcher – Mobile & Web